PAM systems as the key to compliance.
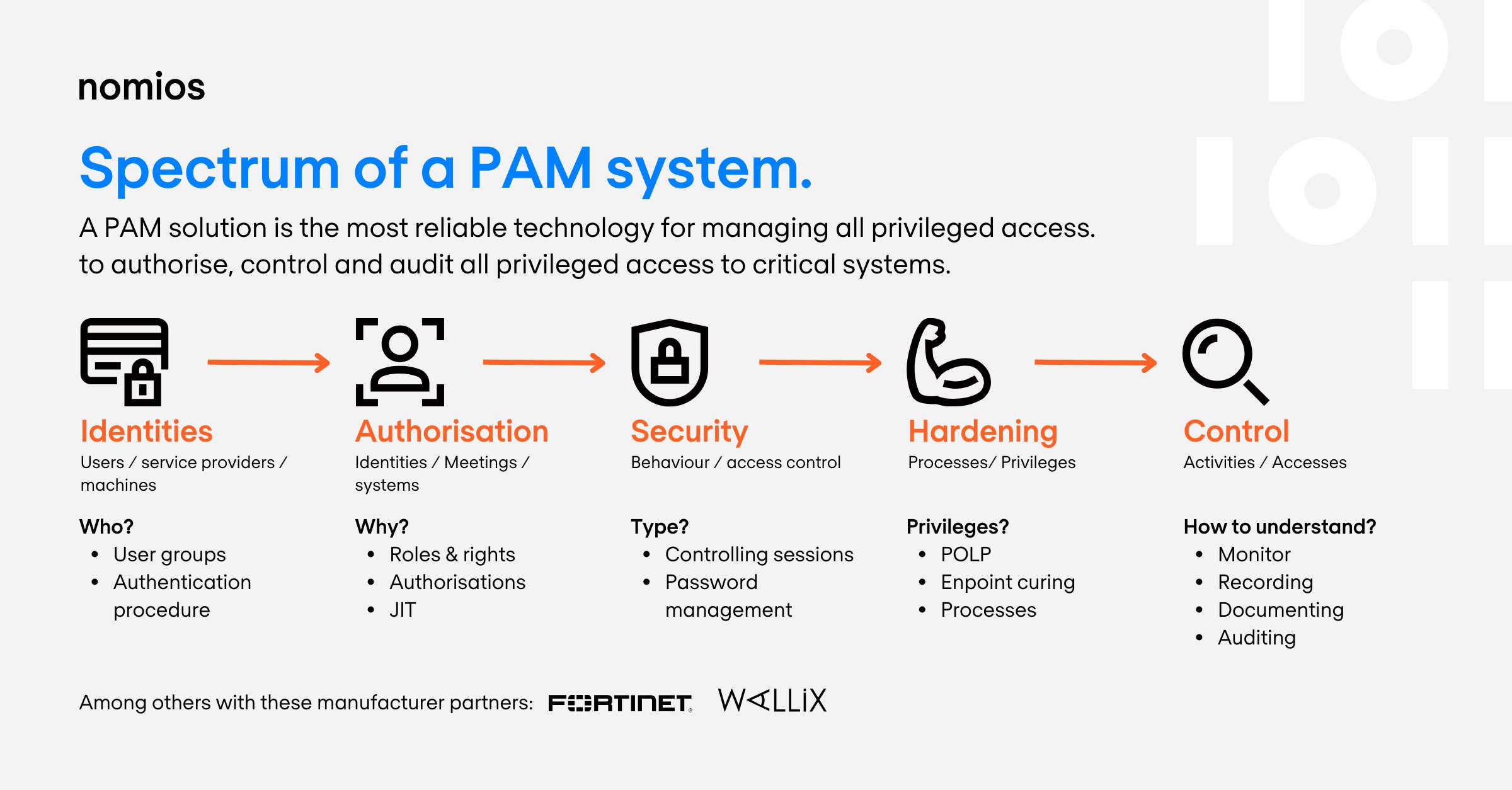
A PAM solution is the most reliable technology for authorising, controlling and auditing all privileged access to critical systems.
Privileged users such as system administrators are increasingly becoming targets of cyber attacks. Privileged access management (PAM) is an effective countermeasure that helps to protect the login data of your privileged users. At the same time, it offers options for restricting privileged access via your existing Active Directory Domain Server (ADDS).
PAM access control protects identities, access data, digital assets (IT&OT) and system access in line with cyber security and compliance standards.
Privileged access control (PAM) is becoming increasingly important, especially in light of NIS-2 and industry-specific standards such as Tisax or IEC62443. GDPR and the overarching ISO27001 standard both require requirements for handling personal data that can be covered by a PAM system.
The overriding principle is that "personal data must be processed in a manner that ensures appropriate security, integrity and confidentiality." Annex A9 of ISO27001 in particular is largely covered by most PAM solutions.
Privileged Access Management comprises the following range of services:
Top 3 use cases.
PAM is suitable for all local and remote human-to-machine and machine-to-machine scenarios with privileged access. However, it always requires well thought-out high availability (HA) and recovery mechanisms.
Adherence to audit and compliance regulations
- GDPR, TISAX, NIS-2 or ISO27001 are just some of the standards that impose strict regulations on privileged accounts. Regular audits of privileged access are crucial for identifying potential security gaps and ensuring compliance with regulations.
PAM for the management of third-party accesses
- Third-party providers or service providers often need access to important systems and data, which poses a considerable security risk if not managed properly. Unmanaged vendor access can lead to data breaches and unauthorised activities.
PAM for Remote Access Security
- With the increase in remote working, including unsecured home networks and personal devices, securing remote access has become of paramount importance.
Solutions from our portfolio
Holistic protection against external threats
Both Privileged Access Management (PAM) and Zero Trust Network Access (ZTNA) are essential components of a robust cyber security strategy. Nevertheless, there are different focuses:
While PAM focuses on securing and managing privileged access to critical systems, ZTNA aims to enforce strict access controls and continuous auditing throughout the network.
Nomios Germany therefore recommends implementing both approaches in order to holistically secure access in IT & OT and protect against external threats.
Your expert for Zero Trust.
Privileged Access Management is part of a holistic Zero Trust architecture, which has only one principle at its core: No user and no application is ever automatically categorised as trustworthy.
Nomios Germany is your partner for successfully implementing Zero Trust in your company. Let us advise you individually and across all manufacturers.