Vulnerability management is the ongoing practice of finding, assessing, prioritising and reducing security weaknesses across your organisation’s technology estate. It covers vulnerabilities in operating systems, applications, network devices and cloud services, plus the configurations and exposed services that can turn a weakness into an incident. The aim is to reduce the issues most likely to be exploited and most likely to cause harm.
Modern environments change quickly. Cloud adoption, SaaS, remote access, APIs and third-party connections expand the attack surface faster than most teams can track. Vulnerability management creates a repeatable cycle that turns detection data into action, so remediation effort reduces risk rather than just shrinking a backlog.
Why vulnerability management matters
Most organisations carry more vulnerabilities than they can remediate within normal maintenance windows. If everything is treated as urgent, teams either burn out or default to generic rules, often driven by severity score alone.
Vulnerability management helps you make better decisions. It gives you a way to agree priorities across security and operations and to answer practical questions: what should we fix first, where are we exposed, and what reduces risk fastest without disrupting the business. It also supports governance by showing that weaknesses are tracked, owned, fixed, and verified over time.
Core elements of vulnerability management
Core elements of vulnerability management describe what you need in place to run vulnerability management as an ongoing cycle, not a one-off project. Each element supports the next, from knowing what you have to proving the fix worked.
Continuous visibility of assets
You cannot manage vulnerabilities without knowing what exists. This starts with an up-to-date inventory of devices, systems, cloud services and applications, plus who owns them. Clear ownership matters because fixes usually sit with IT or product teams, not the scanner.
Discovery of vulnerabilities and weaknesses
Vulnerability management covers more than missing patches. It also includes misconfigurations, exposed services and vulnerable third-party components. The output should be actionable findings with context: which asset is affected, whether it is exposed to likely attackers, and what the impact would be.
Common Vulnerabilities and Exposures (CVE)
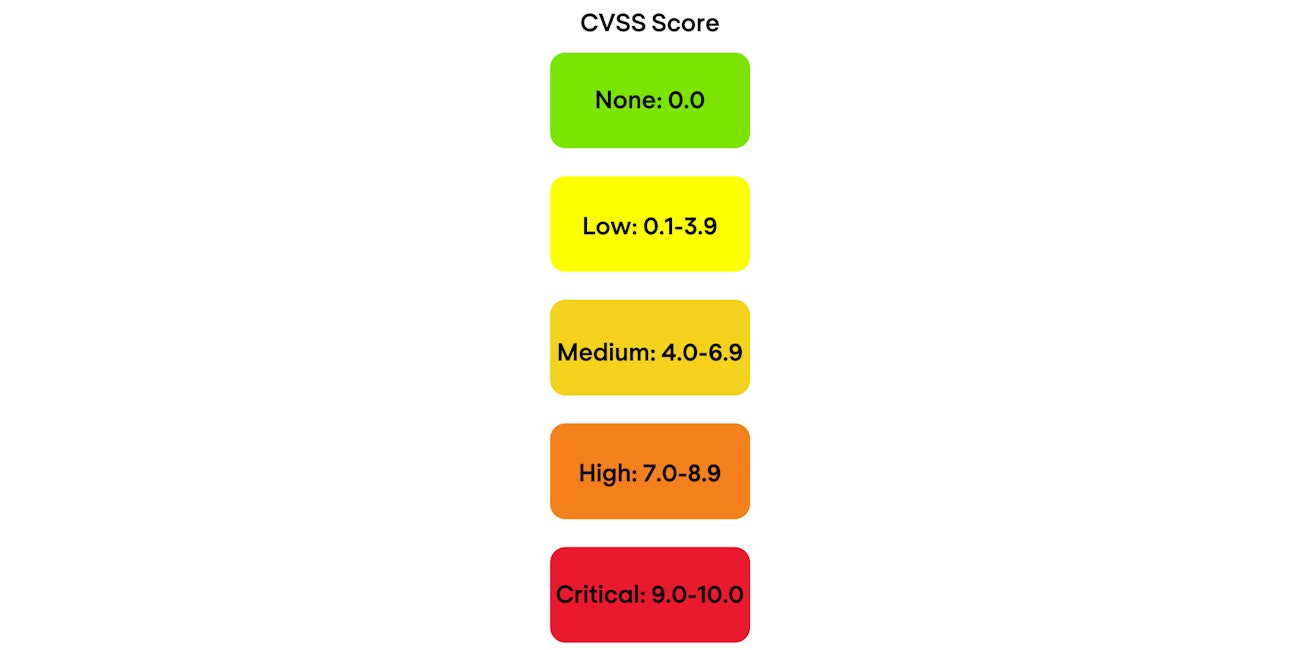
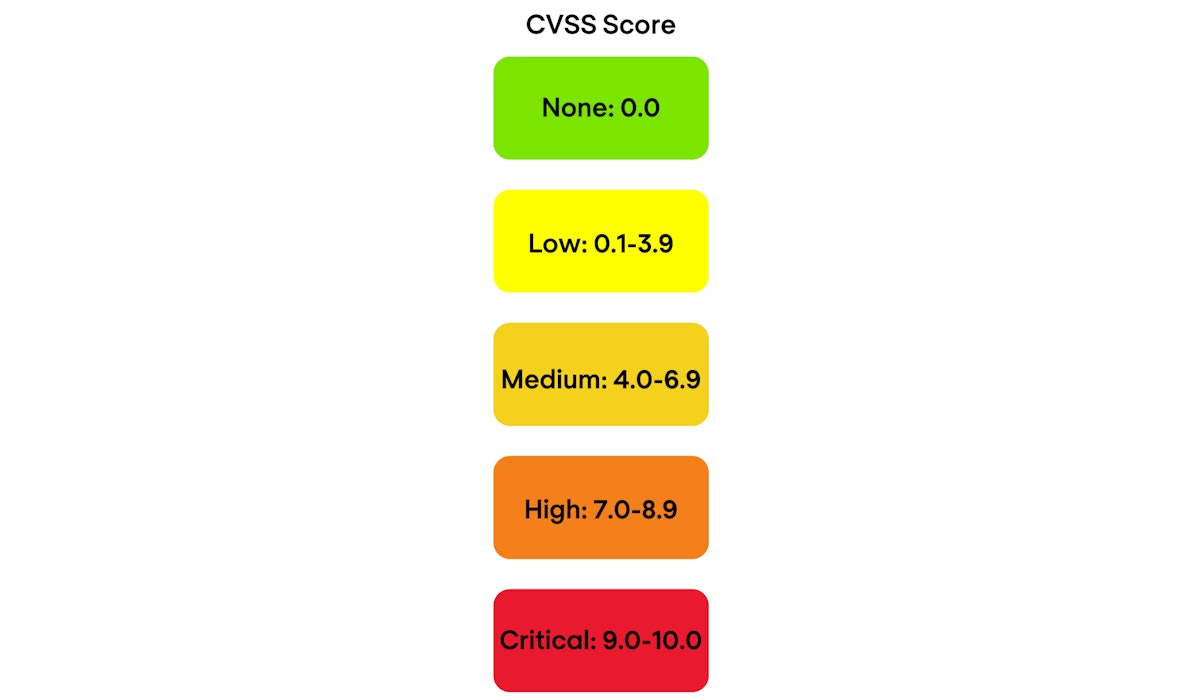
Vulnerabilities that are publicly disclosed are typically tracked using the Common Vulnerabilities and Exposures (CVE) system. A CVE ID provides a consistent reference across tools, vendor advisories and remediation tickets, helping teams confirm affected versions, follow updates and report progress. Severity scoring and exploit context are then used to decide which CVEs to address first in your environment.
Prioritisation that reflects your environment
Severity is a starting point, not the decision. Prioritise using exposure and reachability, exploit signals (for example, when there is evidence the issue is being used in real attacks), and business impact, so the top of the queue reflects real risk.
Remediation and validation
Fix can mean patching, upgrading, reconfiguring, reducing exposure, or applying compensating controls. Always verify closure through re-scanning or targeted checks to avoid “fixed on paper”.
Measurement and continuous improvement
Track coverage, time-to-fix for top priorities, reduction in weaknesses on exposed services, and repeat findings. Vulnerability counts alone can be misleading as coverage improves.
Vulnerability management vs vulnerability scanning
Scanning is a detection method. It identifies known weaknesses and missing updates, and can highlight misconfigurations. Vulnerability management is the operating model around that detection: deciding what matters, assigning ownership, driving remediation, verifying closure and reporting progress.
In other words, scanning produces findings. Vulnerability management turns findings into risk reduction.
How vulnerability management supports zero trust
Zero trust is about limiting implicit trust through least privilege, segmentation and continuous verification. Vulnerability management supports those goals by showing where weaknesses undermine them and by giving a structured way to reduce them.
Common examples include vulnerable remote access services, exposed management planes, weaknesses on identity and authentication systems, and vulnerabilities that allow lateral movement after an initial foothold. When prioritisation accounts for reachability and impact, remediation effort shortens likely attack paths rather than just improving a dashboard score.
Getting started
Start with what you already have, then improve the quality of the cycle. Strengthen asset visibility and ownership first, because they determine whether findings can be acted on. Then tighten detection coverage and the consistency of triage, so the remediation queue is credible.
It also helps to focus on a small set of scenarios that tend to drive real compromise: internet-facing services, identity and remote access platforms, and high-impact systems that support sensitive data or critical operations. As your process stabilises, expand iteratively. Vulnerability management improves with repetition, clear ownership, and verification discipline, not one-off projects.
Nomios can help you set up or mature your vulnerability management programme, from scoping and tooling selection to coverage improvement and risk-based prioritisation. We support you with vulnerability assessments and penetration testing, validation of remediation, and expert guidance on reducing exposure across cloud, network, and endpoint environments so that remediation effort goes to the issues that change risk outcomes.
From vulnerability management to risk exposure management
Vulnerability management is a foundation. It tells you what is wrong with assets and helps you drive remediation. The next step is connecting those weaknesses to real-world exposure: what is reachable, what is likely to be used in an attack path, and what creates the most realistic risk?
That broader view is risk exposure management. It builds on vulnerability management by adding reachability, identity and access factors, chaining of weaknesses, and business context so teams can focus on the exposures that matter most.
Our team is ready for you
Do you want to know more about this topic? Leave a message or your number and we'll call you back. We are looking forward to helping you further.
Related updates

NGFW Firewall
Top 5 NGFW solutions for 2026
Explore the state of NGFW in 2026. Learn how leading next-generation firewall platforms support zero trust, hybrid cloud security, and risk reduction for modern enterprises.

Enrico Bottos

Cybersecurity
Cybersecurity in 2026: Top 10 trends and challenges
Cybersecurity trends for 2026 cover digital sovereignty, quantum security, SSE and identity security, detection, compliance, and managing trust across complex environments.

Richard Landman

Cybersecurity
Top cybersecurity companies to watch in 2026
We selected the top cybersecurity companies to watch in 2026, who have successfully differentiated themselves from other players in the market.

Mohamed El Haddouchi