Would you like 5G or WiFi 6?
Peer insights from wireless industry experts on 5G and WiFi 6 from Mist's VP of Marketing.


CrowdStrike Firewall
CrowdStrike introduces Falcon Firewall Management for cloud-native platform
Cloud-Native Falcon Firewall Management offers simple, cross-platform management of host/OS firewalls from the Falcon console, providing customers with enhanced protection from network threats.


Juniper Networks
Juniper Networks (Mist Systems) Named a Visionary in Gartner Magic Quadrant for Wired and Wireless LAN Access Infrastructure
Mist is included in the 2019 Gartner Magic Quadrant for Wired and Wireless LAN Access Infrastructure. Juniper Networks also recognized by Gartner as one of the Best Wired and Wireless LAN Access Infrastructure vendors of 2019.


Juniper introduces Mist Wired Assurance Service and Marvis Actions
Optimize experiences to network users with Mist Wired Assurance Service. It leverages Mist’s AI engine and microservices cloud to streamline IT operations and simplify troubleshooting across wired and wireless domains.


Security Multi-cloud
Overcoming security challenges impacting multicloud environments
Cloud adoption is increasing at a rapid pace as organizations look for new ways to process, store, and distribute information. For many organizations, deploying new cloud services is much easier than requesting a dedicated set of hardware from IT teams.


Juniper Networks introduces Contrail Insights
Juniper Networks Contrail Insights enhances full stack data center monitoring and automation with single pane of glass visibility.

Legacy laggards or transformation champions
Digital transformation is the new reality for all organisations, and the legal sector is no exception. How are law firms in the UK navigating the journey, and what are they doing to ensure that the opportunities digital delivers aren’t compromised by a lacklustre IT security stance?

A beginner’s cybersecurity guide for board members
Cybersecurity for a board member or business executive, starts by getting acquainted with the CIS Controls, commonly referred to as the CIS 20, says M.K. Palmore of Palo Alto Networks


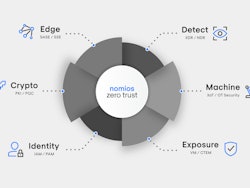
Cybersecurity
Cybersecurity Platforms: 8 Must-Have Attributes
Eight key attributes that should be included in all RFIs/RFPs and become part of every cybersecurity technology platform.


Cumulus Networks Extends Data Center Innovation to Modernize Campus Networks
Cumulus Networks and Dell EMC extend joint benefits of open networking to campus networks and enable a single network OS across data center and campus environments.

Top 5 mobile security threats and how to mitigate them
Some of the biggest mobile security threats companies are seeing recently include: phishing, mobile malware, fake public Wi-Fi connections, malicious apps and data leaks.

Data breach response plan: best practices in 2019
Data breach response plan best practices, enabling companies to retain business, customers, and shift brand perception in the market.

Email security
Decoding Email Security
Email Security expert blog by Kunal Biswas: Email is one of the most popular communication mediums for organisations today. It is also the most prominent attack vector. Emails are being accessed using multiple devices, from different locations, shaping a 'converged device landscape' for email use.
Cybersecurity
Cybersecurity in 2020: A new dawn
What lies ahead in the near future for cyber security? What can we expect? In this blog I'll attempt to answer what cyber security might look like in 2020.

The dark side of governments: A growing threat of APT groups
For most nation states, covert advanced persistent threat (APT) groups are an equally valuable tool that operate in the shadows, stealing data, disrupting operations, or destroying the infrastructure of targeted enemies.

Network security
Top 5 Network Security Solutions and Technologies
The 5 best Network security solutions and technologies that help define and guarantee business success. Unfortunately many enterprises do not know what network security solutions are essential to securing their network and data.

Endpoint security EDR
5 Endpoint Security Best Practices
Your Cyber Security strategy should include Endpoint Security, as it is one of the most critical components for network security. In this article, our experts sum up Endpoint Security best practices for the Enteprise.


Fortinet Wins SE Labs Best Network Security Appliance Award
Fortinet has been awarded the Best Network Security Appliance award from SE Labs – one of the most respected labs in the testing community. SE Labs has been testing FortiGate products for the past three years, and in addition to this accolade, have awarded a AAA rating to the FortiGate solution for the third year in a row.
Sign up for our newsletter
Get the latest security news, insights and market trends delivered to your inbox.